Computing Facilities Guide
1. IT Facilities at Magdalene
The IT Office is responsible for all matters relating to the use of the College Network and provision of computing facilities and support for administrative staff, students and fellows. The IT Office is located in the Lutyens Building (Benson E3) on the West side of the college and is manned 9.00am – 5.00pm. Outside of these hours, for emergency support only, the Porters’ Lodge should be contacted: they will make contact with a member of the IT Office staff.
1.1.1 Staff
The IT Office is manned by the following full time staff:
Head of IT: Mark Crane
Windows Systems Administrator: Nick Grange
IT Systems Administrator: Usman Zia-Ul-Haq
IT Technician: Liam Mason
IT Office staff can be contacted during office hours by telephone on (3)32127, or at the following email address: it-support@magd.cam.ac.uk
1.1.2 Cleaning Infected Machines
Although the IT Office has no duty to clean or rectify problems with a Student’s personal machine, it does provide this service when operationally possible. No responsibility can be taken for any loss of work or damage to the computer while it is left with the IT Office. Obviously, the IT Office will take great care not to cause any loss, but it is the duty of the owner to ensure that their work is backed up. If, as part of the clean up process, it is necessary to reinstall any software, the owner must provide the required media (CD/DVD’s) and legitimate software licences to use. During the cleanup process, any inappropriate software which is known to be or is a potential cause of problems will be removed. One of the biggest problems faced by the University is use by Students of inappropriate peer-2-peer software to download unlicensed copyrighted material. Please see the sections titled ‘Network Use’ and ‘peer to peer file sharing’.
1.1.3 Providing Technical Assistance
The IT Office will provide technical advice and assistance where it can. This can be to do with using the college computers or personal computers or advice on purchase of computer equipment.
1.1.4 Hardware Support
The IT Office will provide support and advice for problems concerning hardware, if it is unable to help then the owner will be directed to the University hardware support service. They can provide extensive support for all computers and data recovery, however, this service is not free.
The College is connected to the Cambridge University Data Network (CUDN), which covers the City and other local institutions. In turn, the CUDN is connected to the Joint Academic Network (JANET) which connects the UK’s education and research organisations to each other as well as to the global Internet. The CUDN provides access to JANET and the Internet at speeds of up to 10Gb/s. Each of the institutions connected to the CUDN maintain their own networks, Magdalene is connected to the CUDN via a 1Gb/s link. The network infrastructure within the College provides 100Mb/s connection in all student rooms.
There are a number of computers provided for general use principally in three locations: Benson Court E1, the College Library and Cripps Court Computer Room. There are Windows PCs installed with Microsoft Office software.
Access to the machines is controlled by a user ID and password. Your UserID to login to the College computers is the same as your CRSID (see section 2.2 Retrieving your CRSID), the default password is ‘Gardetafoy1.’
The first time you log in to a computer you will be prompted to change your password.
It is important that when you have finished using the Computers you must logoff, failure to do so could make you liable to print charges through someone else using your logon.
Access to the buildings is controlled via your University Card. Currently each student is initially allocated 8GB of storage on the server which is backed up daily.
All College Student machines are maintained by the IT Office. Any problems with these machines should be reported to the IT Office, this includes problems with printing and resetting forgotten passwords.
1.3.1 Andrew Clarke Suite (Mallory Court)
- 3 x Windows 10 with dual monitors
- 1 x 27″ Monitor with connections for personal laptop
- 1 x Sharp MFP Photocopier for printing and scanning
- 1 x Large format paper trimmer
1.3.2 College Library
- 4 x Windows 10 with single monitor
- 1 x Terminal on 1st floor for library catalogue
- 2x Sharp MFP Photocopier for printing and scanning, on both 1st and 2nd floors
1.3.3 Cripps Court computer room
- 3 x Windows 10 with single monitor
- 1 x Sharp MFP Photocopier for printing and scanning
1.3.4 Basing House Hostel
There is a Windows 10 based PC with standard software installed.
The IT Office have a limited number of loan laptops that can be offered in the case of a failure of a students personal computer. Students should note the guidance in section 3.3 regarding having a well maintained computer and a Computer Recovery Plan in place.
Priority of a loan laptop is given based on the below;
-
- Students who need to take their own laptop into an exam.
- Students with learning difficulties where use of a computer is essential/highly beneficial, and use of a machine in the College Computer Room, or elsewhere, does not offer the same benefit or sufficient versatility.
- Students who need their own computer for coursework, where use of a machine in the College Computer Room, or elsewhere does not offer the same benefit of sufficient versatility.
- For general work, revision, etc, again where use of a machine in the College Computer Room, or elsewhere does not offer the same benefit of sufficient versatility.
Students will need to discuss their situation with their tutor, who will need to endorse the loan from the IT Office before the loan is made.
Loans are made for a maximum of three weeks, which should be ample time for Students to implement their Computer Recovery Plan.
1.5.1 Printing
Students may use any of the printers in the Andrew Clarke Room, New Library, Cripps Court Computer Room and Peypes Left Cloister by logging into one of the college computers.
Students will need to do the following before printing;
- Log in to a college computer
- a. if this is the first time you have logged in, you will need to reset the password you have been given, and you MUST wait 24 hours for the new password to be passed to the printing system before proceeding to the next step.
- Open your document and navigate to the print menu, and click print.
- Place your college card on card reader of the printer.
- On the printer screen the Papercut application will ask you to put in your username and password, this registers your card against your CRSID.
- Once registered you will be shown a list of your prints awaiting release
- Choose the documents you wish to print and they will be printed.
When you next come to print follow steps 1 -3 which will log you into the printer and allow you to release prints.
Printing is charged as per the below;
Black & White;
- Single side – £0.06 pence per sheet
- Double sided – £0.08 pence per sheet
Colour;
- Single side – £0.10 pence per sheet
- Double sided – £0.15 pence per sheet
All printing charges are added to a students college bill at the end of the term.
The printer is filled with standard 80gsm laser paper, personal paper up to 180gsm can be used via the multi-purpose tray.
1.5.2 Web Print
Once you have completed the above setup you can also use this url (you must be connected to Wi-Fi via eduroam in college for this to work) to check your balance and submit print jobs, you can then collect the printout from any of the printers mentioned above within six hours.
https://stu-print.magd.cam.ac.uk
1.5.3 Mobility Print
TBC
1.5.4 Photocopying
All printers are capable of photocopy, you will need to present your college card to select this function. Costs per page are the same as printing above.
1.5.5 Scanning
All printers are capable of scanning, you will need to present your college card to select this function. The scan will then be emailed to your college email address.
At various locations in the University there are public rooms with DS (desktop services) machines which are maintained by the Computing Service. These machines have all of the standard software installed and also course specific software too. Access to these machines is via your CRSID and password. You can access your DS-filestore space from your personal computer, instructions on how to do this can be found here:
https://help.uis.cam.ac.uk/service/desktop-services/ds-filestore
Please note that the Windows based college Student computers are not set up as DS machines. We do however maintain a subset of the DS software on them.
2. CRSID, Email & Multi Factor Authentication
Your CRSID is used extensively throughout the College and University as your ID. It is usually made up with your initials followed by some digits. e.g. abc123. A centralised authentication system, known as Raven, uses the same ID as does the University email system, your email address will be ‘yourcrsid’@cam.ac.uk.
For information about how you retrieve your CRSID please visit this webpage https://help.uis.cam.ac.uk/service/accounts-passwords on the University website.
Full information about the University email system and how you can access it can be found here: https://help.uis.cam.ac.uk/service/email
Multi-factor authentication (MFA) adds an extra layer of security to your CRSID. It’s sometimes also called two-step verification or two-factor authentication (2FA). You’ll occasionally need to provide an additional form of identification to sign in – for example, a code sent to your mobile phone.
You’ll need to set up your 2FA method when you first sign into your account. After that, you’ll need to use one of these factors occasionally to confirm your identity when accessing your account.
All details on how to set up and manage your 2FA methods can be found here;
Set up multi-factor authentication | IT Help and Support (cam.ac.uk)
The IT Office strongly advise you set up more than one 2FA method as if one method fails (e.g. a mobile phone is lost or broken), the other can be used to continue to gain access and manage your 2FA methods.
Set up your second factors for authentication | IT Help and Support (cam.ac.uk)
3. Use of Personal Computers
The college provide computing facilities including a number of computers that students may use, as outlined in section 1.3, however students are reminded that they should expect they will need their own computer to in order to complete their studies. Using a personal computer will enable students to do research, complete notes and course work and undertake exams while in they are in their accommodation or otherwise outside of the college or University provided computing areas. Students should ensure that the computer they have is appropriate for their studies, that it will run any software that is required by their course including any exams software they will need.
Students are advised to discuss this with their tutor at the start of term so that they can ensure they have the right equipment in place at the start of their studies.
Students are advised to ensure that they keep regular backups of their data on their personal devices to either to physical media such as USB Key’s or a Cloud storage solution such as Microsoft OneDrive, Google Drive or Drop Box.
Students are reminded that it is their responsibility to undertake regular maintenance of their computer to ensure it remains functional, including keeping software and operating systems up to date with security and functionality patches (see more in section 5.2). Students should also be aware of the importance of protecting their device from physical damage either while in use or in transit. Computers are often damaged by rain coming in through open windows and students should choose carefully where their devices are kept while they are not in their room.
All Students should prepare a Computer Recovery Plan in the event that their computer stops working for any reason. The college computers are always available (see section 1.3) however students should consider having a stand-by computer available from home or some other arrangement, if using the college provided computers in the Library, ACS or Cripps computer rooms isn’t sufficient.
Most new computers will come with manufacturer’s Warranty, however these are generally quite limited and require the device to be returned to the manufacturer for repair. Students should familiarise themselves with the details of any warranty that their computer may have, how to contact the provider of that warranty, and, should the warranty have expired, consider if taking out an extended or third party warranty is appropriate.
Students must know what they will do in the event of their computer failing so that they can continue to access a computer, while theirs is being repaired.
4. Connecting your Personal Computer to the Network
The College wireless network is accessible in the majority of locations and work is ongoing to improve this further.
There are two wireless networks visible:
- eduroam
- Magd-IoT
eduroam
This is the colleges primary Wi-Fi network for use by all college students. This is part of a global academic wireless provision which provides internet access using your locally provided access token. It is available in nearly all Colleges and Departments as well as the majority of Cambridge city centre. Students can retrieve their eduroam token by going to https://tokens.uis.cam.ac.uk/ using their Raven logon. Once they have this token, the logon ID is their full Cambridge email address and the password is the token retrieved.
Students can find out more about eduroam and how to connect here: Connect to eduroam wifi | IT Help and Support (cam.ac.uk)
Magd-IoT
Magd-IoT is the replacement service for magd-local and is available to members of the college only and is for use on devices that cannot be connected to eduroam. Guidance on how to connect to Magd-IoT can be found in section 4.4.
All college rooms have Wi-Fi coverage and nearly all also have at least one wall socket Ethernet connection. Students should contact the IT Office if either the Wi-Fi our Ethernet network socket are not working optimally.
In order to use the Ethernet wall connection students will need to use a patch cable, and connect it to their device. Students should be aware that not all computers have an in-built Ethernet port, so should be prepared to source the appropriate adaptor for their device.
The location of the wall sockets is not always in a convenient position for students desks therefore, the length of the patch cable students will need will vary from room to room. Patch cables in various lengths are available from the IT Office free of charge.
We do not allow the use of personal wireless routers as they can have a detrimental effect on the College network. If your Wi-Fi signal is poor please report this to the IT Office who will look into this for you.
Magd-IoT
If your device will not connect to eduroam, you may connect that device to Magdalene’s new Wi-Fi Service Magd-IoT. To do this, you will need to connect to the ClearPass portal from a computer that is already connected to eduroam here in college, and create a device.
https://clearpass.magd.cam.ac.uk/guest
To add a device to ClearPass you will need to know it’s “mac address”. Information on how to find the mac address of the most common devices can be found in the section 4.5 below.
Once signed into the ClearPass portal, the first page will show any devices you have already added. If this is your first time in the portal, click the “Create” button to get started.
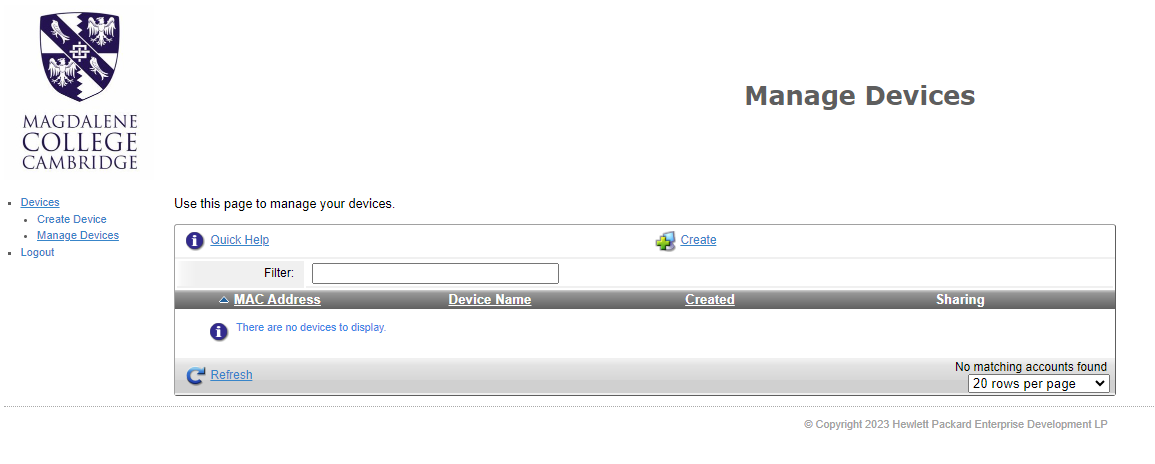
On the “Register Device” page, give the new device a name and type in the mac address. Then click “Create Device”. A window should pop up stating that creating the device was successful.
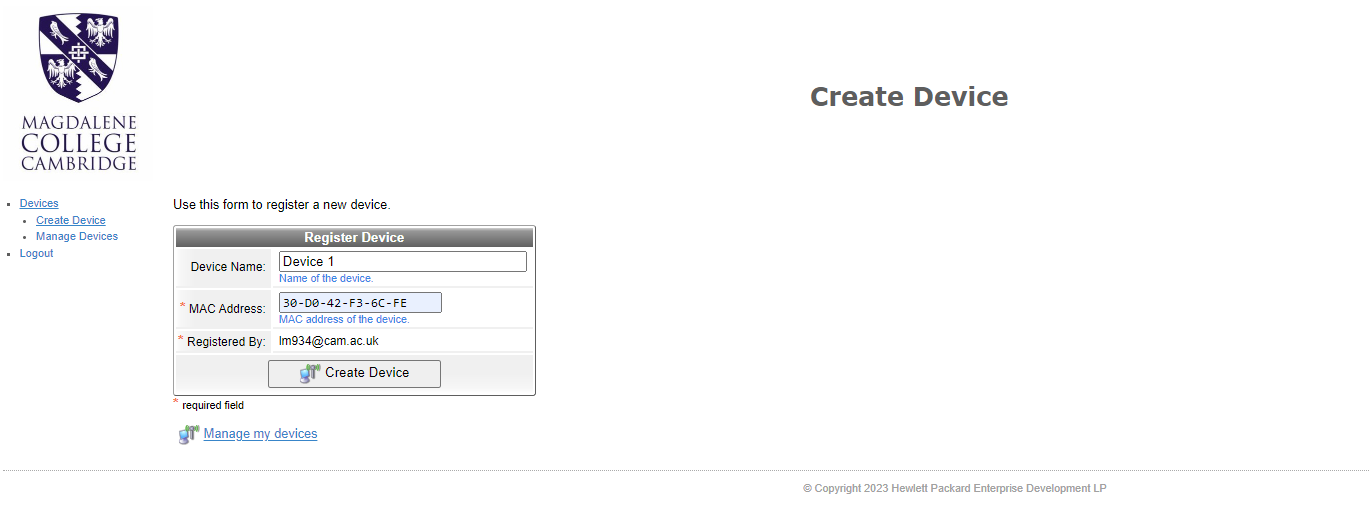
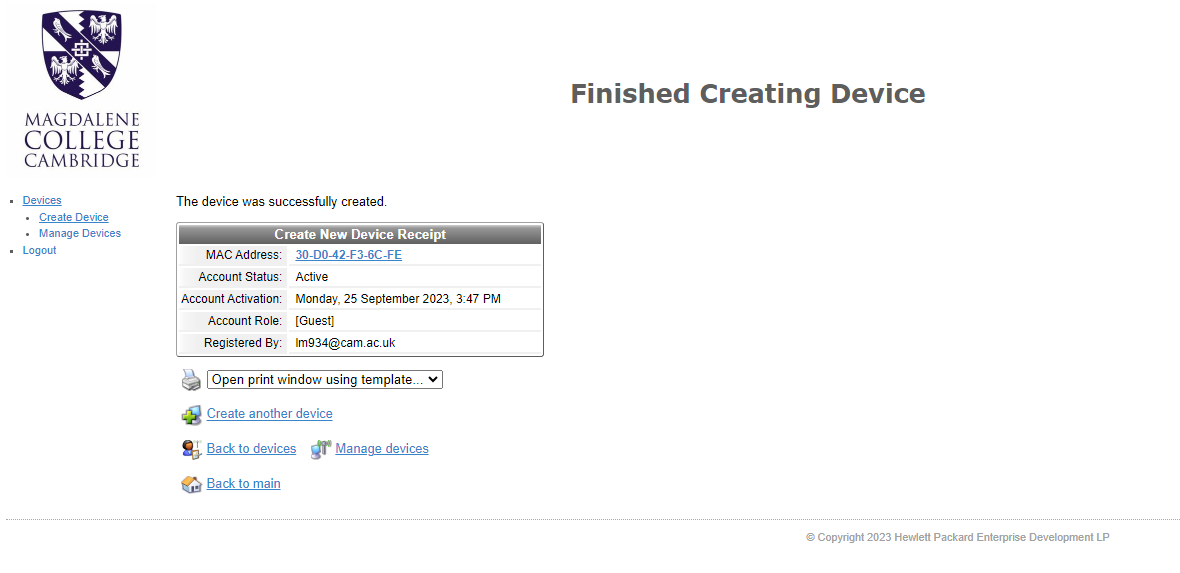
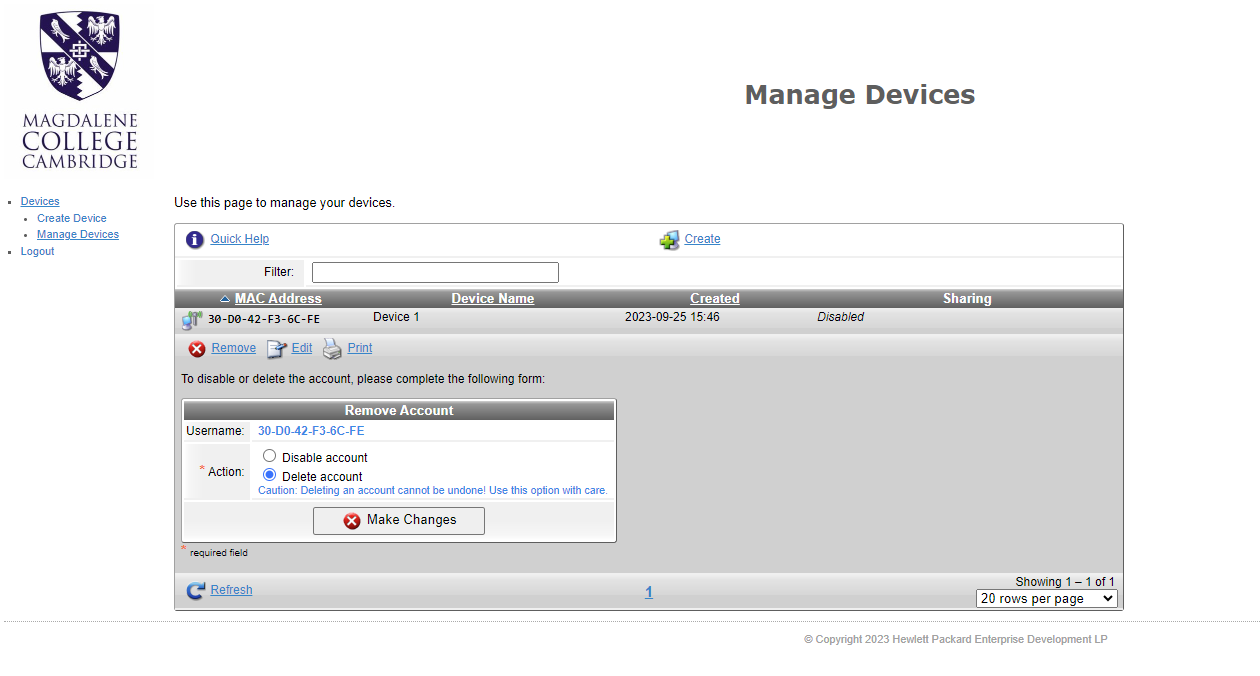
Click “Manage Devices” in order to see the devices you have created. From here you can click a device to update it (if the device should change for any reason) or delete it.
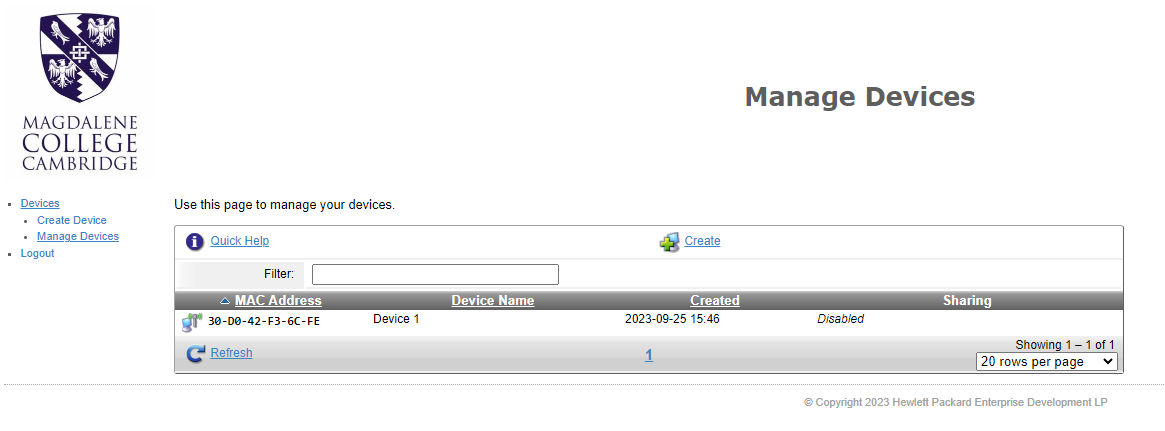
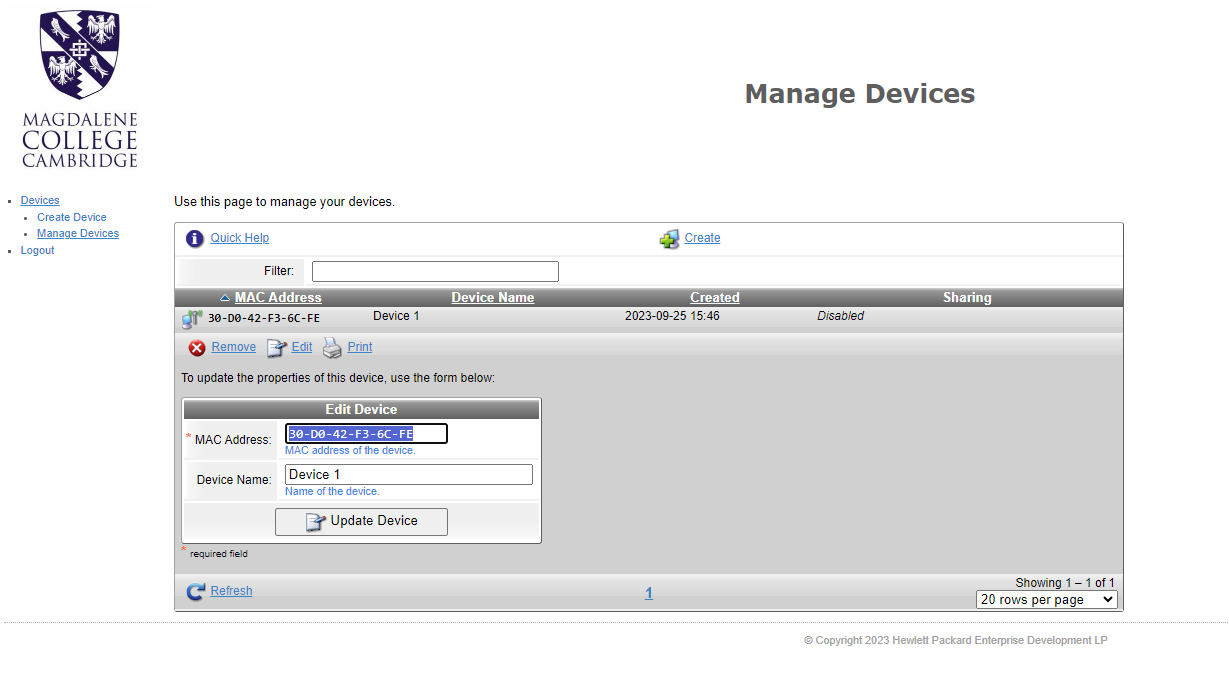
Once the device has been created in ClearPass, you will be able to connect to the Wi-Fi network “Magd-IoT”.
Students will be allowed to connect 2 devices to ClearPass, either Wi-Fi or wired.
Below are instructions on finding the MAC address of common devices that might connect to Magd-IoT;
Amazon
Amazon Echo
- Download the Amazon Alexa app to your phone or computer from the app store.
- Sign in with your Amazon account.
- On your phone connect to the wireless network transmitted by your Echo device.
- The wireless MAC address for your Echo can be found at the bottom of the Echo Setup screen in the Alexa app.
Fire Stick
- From the Amazon app, visit the Home
- Choose Settings.
- Choose My Fire TV or Device.
- Choose
- Choose Network.
- The wifi MAC address should be located under MAC Address (Wi-Fi).
Nintendo Consoles
Nintendo 3DS, 3DS XL, or 2DS
- Go to System Settings.
- Select Internet Settings.
- Select Other Information.
- Select Confirm MAC address.
- The MAC address is displayed on this screen.
Wii U
- From the Wii U Menu, select System Settings.
- Using the Left Stick select the Internet icon and press the A Button.
- Select View MAC Address and wait a moment for the MAC Address to be displayed.
Nintendo Switch
- From the Switch’s Home menu, go to System Settings
- Scroll down and select Internet.
- The MAC address will appear under System MAC Address.
Sony Consoles
Playstation 3
- From the main menu, select Settings.
- Select System Settings.
- Select System Information.
- The MAC Address will then be displayed on the screen.
Playstation 4
- Arrow up and over to Settings in the PS4 menu.
- Scroll down to Network
- Scroll down to View Connection Status
- Note both MAC addresses listed (one for Wi-Fi and one for LAN cable).
PlayStation 5
- Go to Settings.
- Select System.
- Select System Software.
- Select Console Information
- Note both MAC addresses listed (one for Wi-Fi and one for LAN cable).
Microsoft Consoles
Xbox 360
- Select System Settings.
- Select Network Settings.
- Select Configure Network.
- Under Basic Settings check to make sure IP Settings is set to Automatic.
- Go to Additional Settings.
- Select Advanced Settings.
- The MAC Addresses for the wired and wireless adapters should be displayed.
Xbox One / Series S & X
- Press the Xbox Button on your controller.
- Select Profile and System and then Settings.
- In the settings pane, select General and then Network Settings.
- Select Advanced Settings.
- The MAC Addresses for the wired and wireless adapters should be displayed.
Streaming Devices
Apple TV
- With your Apple TV remote, navigate to the Settings icon and select it.
- From the Settings menu, select General.
- Under General, select Network.
- Your MAC Address will be next to either Wi-Fi Address or Ethernet Address depending on whether you are connected to the internet via Wi-Fi or a Wired connection.
Roku/Roku Express
- On the back on your Roku there are a pair of six 2-digit pairs separated by colons, e.g. 00:0D:0A:1H:3G:5C. One set is for the Ethernet connector and for the other for the wireless connector.
- Alternatively, from the Roku home screen, select Settings > Network > locate the value next to “Wireless MAC Address”
Smart TV/Bluray Player
- Most MAC Addresses will be visible in the Settings Menu, either under the Network or About sections.
- Alternatively, check with the manufacturer for instructions on how to obtain the MAC Address for your specific model.
5. Security
Cambridge University has been and continues to be a prime target for hackers from all around the world, so it is essential that security is taken seriously.
Students need to be vigilant against any threats to their own or the wider colleges computer systems and data. Students are reminded that they are personally responsible for the security of their device and the following should help inform them on how to minimise any associated risks.
Operating systems and software applications are constantly being updated to fix flaws both in their functionality and security. Most of these updates are available free of charge from the relevant company websites.
Most operating systems have automated update systems. In the case of Microsoft Windows ‘Automatic Updates’ should be enabled, so that new patches and updates are downloaded and installed on a regular basis. MacOS X systems have a ‘Software Update’ facility which should be run on a regular basis. Since MacOS X machines are beginning to be targeted more by hackers, it’s vital that patches are applied. Linux and other UNIX like systems also need to be updated on a regular basis too. The way that updates and patches are applied on these systems varies.
Students should familiarise themselves with the process for updating their computers with these patches.
It is absolutely essential that Students machines have anti-virus software installed and that it is kept up to date. Most new machines are supplied with anti-virus software pre-installed but these will normally expire after three months to a year.
It is important that students do not install more than one antivirus program as this could impact the functionality of both programs. Students should remove any pre-installed antivirus programs if they do not wish to purchase them at the end of the initial trial period before installing an alternative program.
Cambridge University has a site license for Trellix anti-virus software which is available free to all users of the University network, details below;
4.4.1 Types of Virus
Trojan Horses
As the name suggests, a Trojan horse program is a program that pretends to be something that it is not. A user is enticed to download them and run them manually (as Trojans don’t spread on their own). Once run, these programs install themselves so that they are started up each time the computer is turned on. Trojans have a wide range of uses, from hijacking/redirecting web traffic to opening ‘back doors’ on systems to allow hackers remote access.
Worms
A Worm is typically a small program which spreads very rapidly over a computer network, typically by exploiting a known bug (typically a buffer-overflow) in an operating system or application. Many worms use email to spread themselves. Worms like Trojans get added to the start-up programs on a system, and typically interfere with anti-virus and other Magdalene College Cambridge Computing Facilities Guide Page 11 of 16 security software. Worms can make systems unusable by slowing them down to a crawl or by having an immediate payload which can be destructive.
Boot Sector
This type of virus replaces the ‘boot sector’ of the PC which contains the program that enables a computer to start up. This type of virus is not very common these days, since these were typically spread by booting from an infected floppy disk.
Parasitic Viruses
Also known as file viruses, these attach themselves to a specific program (or ‘executable’), or to all programs on a system. Once a system is infected it may behave strangely and some programs may not work anymore. Anti-virus software may not be able to repair systems which are heavily damaged – requiring all of the infected software to be reinstalled from scratch.
Macro
These take advantage of built in macro commands that are embedded in files and run automatically. These are most commonly found in Microsoft Office documents particularly Word and Excel. Once infected, any new or existing document opened on that system will become infected.
Hoaxes
Hoaxes are reports of non-existent viruses. Typically they arrive as emails which warn of new viruses or security problems and ask you to email everyone you know. Hoax emails will often ask you to delete legitimate files from your system which prevents it from working properly.
In recent years the threat from viruses has been brought more or less under control, but a bigger problem showing enormous growth is ‘spyware’ and general ‘malware’. As the name suggests ‘spyware’ is software that collects information about your activity and then returns this information back to a remote system.
‘Malware’ is typically a piece of software that gets installed without your knowledge. These are typically search bars, links to premium rate services appearing in your programs menu etc.
Both of these classes of software pose a security threat to you. These programs also tend to make your machine very slow. A lot of current ‘spyware’ and ‘malware’ is becoming viral in nature making them increasing act like viruses (and thus making them difficult to remove). A clear indication that your machine has become infected is that your web-browser opens up lots of annoying pop-up windows.
Ransomware is a type of malware which uses cryptovirology to create malicious software that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them. In a successful cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem. Having good backups of all your work is the best way to mitigate your exposure to his threat, engaging with any ransom demand is not recommended.
Ransomware attacks are typically carried out using a Trojan that is disguised as a legitimate file that the user is tricked into downloading or opening when it arrives as an email attachment. However, one high-profile example, the “WannaCry worm”, travelled automatically between computers without user interaction.
Mac and Windows machines have a personal firewall built in, which should be turned on. The Windows firewall needs to be configured to allow ‘ICMP incoming echo requests’ (required by the University). If students are using an operating system which doesn’t have a firewall built in then they should consider installing a third party one.
The IT Office can advise further on this or any of the above if required.
Please visit this page on the University website which points out what to look for and advice when going online:
https://help.uis.cam.ac.uk/new-starters/it-for-students/student-it-services/stay-safe-online
There is also this Moodle interactive tutorial which will raise you awareness and takes 30-40 minutes to complete: https://www.vle.cam.ac.uk/course/view.php?id=137361
6. Network Use
Although the College is connected to the Internet at 1Gb/s this is shared by over 600 connections. Generally, the response times are very good compared to a normal broadband connection. However, it doesn’t take many people downloading large files simultaneously to reduce the speed of the network for everyone. Using the Internet for normal web browsing, email and messaging will generally not cause problems for anyone, but other activities can. In the interests of enabling the majority to experience a fast network you are asked to follow the rules and guidelines given here.
The University receives notifications from various agencies about copyright material that has been downloaded illegally and passes these to the IT Office for action. The IT Office is required to immediately disconnect the offending machine and confirm that all copyright material has been removed. The person who has registered that machine on the network will receive an automatic fine of £50.
All use of “peer-to-peer file sharing” software for sharing copyrighted music, videos or software is forbidden. Kazaa, eDonkey, Bearshare, LimeWire, iMesh, Gnutella, WinMX and BitTorrent amongst others are of particular concern, as they are mostly used to download and redistribute copyright infringing music and video material. Other peer-to-peer software such as Skype (see below) can also generate substantial amounts of traffic.
NB. Students total network usage is calculated as the sum of all incoming and outgoing traffic external to the University and all excess of a students allowance will be at their expense.
Video calls have almost become the standard for keeping in touch however, they do consume a large amount of data particularly if they are using HD video. According to the Skype website:-
The bandwidth required by Skype depends on the type of calls you want to make. The table below provides the minimum download and upload speeds required, as well as the recommended speeds for best performance.
| Call type | Minimum download / upload speed | Recommended download / upload speed |
|---|---|---|
| Calling | 30kbps / 30kbps | 100kbps / 100kbps |
| Video calling / Screen sharing | 128kbps / 128kbps | 300kbps / 300kbps |
| Video calling (High Quality) | 400kbps / 400kbps | 500kbps / 500kbps |
| Video calling (HD) | 1.2Mbps / 1.2Mbps | 1.5Mbps / 1.5Mbps |
| Group video (3 people) | 512kbps / 128kbps | 2Mbps / 512kbps |
| Group video (5 people) | 2Mbps / 128kbps | 4Mbps / 512kbps |
| Group video (7+ people) | 4Mbps / 128kbps | 8Mbps / 512kbps |
The bandwidth required by Zoom depends on the type of calls you want to make. The table below provides the minimum download and upload speeds required, as well as the recommended speeds for best performance.
| Call type | Minimum download / upload speed | Recommended download / upload speed |
|---|---|---|
| 1:1 Video Calling | 600kbps / 600kbps | 1.8Mbps / 1.8Mbps |
| Group Video Calling | 1Mbps / 800kbps | 3Mbps / 3Mbps |
The bandwidth required by Teams depends on the type of calls you want to make. The table below provides the minimum download and upload speeds required, as well as the recommended speeds for best performance.
| Call type | Minimum download / upload speed | Recommended download / upload speed |
|---|---|---|
| 1:1 Video Calling | 500kbps / 500kbps | 1.5Mbps / 1.5Mbps |
| Group Video Calling | 1Mbps / 500kbps | 2Mbps / 1Mbps |
Streaming services such as Netflix, Amazon Prime and BBC iPlayer can cause a large amount of data to be transferred into the College network.
Using these services should be done sparingly and only when absolutely necessary. While the IT Office understands that these services are very popular, and that the college network connection is fast, unlike a home broadband connection, it can only support so many concurrent streams. In a home scenario there may be up to 5 or 6 users of online services, here at college there could be in excess of 300. Please consider this when choosing to use a streaming service and use alternatives where possible, e.g. digital terrestrial TV and Radio services, or download to watch or listen later.
Any use of the Cambridge University Data Network (CUDN) is governed by the University Computing Service and users are advised to familiarise themselves with these rules and guidelines. Ignorance of them is no defence either in law or in University/College-determined jurisdiction. Breaches of the rules will be investigated by the University Computing Service and the Magdalene College IT Officers will do all they can to assist them. The terms and conditions of use issued by the Computing Service can be found at the following link:
Information Services Policies, Rules and Guidelines: https://help.uis.cam.ac.uk/isc-rules/
This section outlines the main rules and regulations for the use of the College Network.
- All use of “peer-to-peer file sharing” software for sharing copyrighted music, videos or software is forbidden.
- Always apply the latest security updates for your operating system and other software, which are available from the manufacturers’ web pages, for example, Windows updates are available from the Microsoft Windows update web site.
- The College accepts no responsibility for the integrity of data stored on College equipment. The onus is on the individual to backup any data files in their personal disk space.
- The use of any College facility to transmit, store or display offensive material is forbidden. This point should be borne in mind if posting to social media.
- It is forbidden to use the Magdalene Computer Network as a forum for any commercial organisations.
- All users are expected to take reasonable care not to introduce viruses into the network. Anti-virus software must be installed and kept up-to-date. (Refer to section 5.3 for further information).
- All shared equipment faults should be reported to the IT Office.
Changes and amendments to these rules may be posted on the notice boards from time to time.
Breaches of these rules will be dealt with by the I.T. Committee or the Master as appropriate. Depending on the outcome of any investigation, appropriate disciplinary action will be taken, including the removal of rights to use the College Computing Facilities.
Any fines and all charges for services taken that would incur such a charge, e.g. printing, will be added to the students college bill at the end of term.
7. Useful Websites
MagNet Access Instructions
- Go to the College website at https://www.magd.cam.ac.uk
- Click on the ‘MagNet’ link in the top right hand corner
- Scroll down the page and click the ‘Log in with Raven’ button
- You will be automatically redirected to the Raven log in screen
- Fill in your Raven login details and click ‘Login’
- You will automatically be redirected back to the Magdalene website
- There will now be a ‘For Students’ link on the left of the top navigation line, if you click on these this you will access the internal pages.
The University Information Services website contains a wealth of information of all aspects of computing and services available in the university. The site covers everything from Rules and Regulations, Email, Software sales and Training courses to Printing, Photography, Videoconferencing and Health and Safety.
The University Information Services homepage: https://help.uis.cam.ac.uk
University Email service: https://help.uis.cam.ac.uk/service/email
Retrieving your CRSID: https://jackdaw.cam.ac.uk/signup
Retrieving your eduroam token: https://tokens.uis.cam.ac.uk

